Empower IBM i to conduct its own compliance verification and enforcement.
IT professionals often complain about the burden of managing security and maintaining compliance. As an added challenge, IBM i staff typically lack formal (or even informal) training in these disciplines. Risk is elevated when organizations ignore the reality that most Power servers operate without adequate security controls.
Security Starts and Ends with an Assessment
Many people concerned with their security stance delay action because they don’t know where to start. Experts agree that an assessment of current vulnerabilities is the best place to begin. PowerTech recommends an initial Security Scan, a painless procedure performed using a specialized software tool at no cost to the recipient. For a more comprehensive review, HelpSystems can perform a deep-dive assessment or conduct penetration tests.
A recurring assessment cycle validates progress and determines when additional action is necessary. It also shows whether established policies are being followed. In fact, proof of policy adherence is a primary goal of most regulatory audits.
Time for Cleanup
Vulnerabilities should be documented and then resolved. Mitigating security risks typically requires a combination of software and services, provided by either skilled internal staff or external consultants. HelpSystems, highly respected in the IBM i security industry for its PowerTech software brand, recently expanded to include SkyView Partners, adding to its extensive product portfolio and introducing a complementary suite of security services.
Cleanup activities may include migrating the server to a higher security level, improving the strength of the password policy, reducing the number of users with administrative privileges, and gaining audit visibility and control of connections that originate from users' PCs. Some corrective actions can be implemented quickly, providing "quick wins" in the war on risk.
For many organizations, the cleanup phase can take considerable time. Years of neglect and misconfiguration are seldom corrected overnight. Security initiatives should be divided into more manageable sub-projects, each contributing to the project's overall success.
"Now What?!"
Security projects are never truly complete, and they will ultimately fail if treated with a "set and forget" mentality. Policies must be reviewed regularly—some experts suggest annually—and evolve to accommodate the adoption of new technologies as well to address new risks that appear on the ever-changing threat landscape.
Ongoing verification of policy adherence is imperative to ensure the server remains in the desired state. Manually reviewing system values, user profile attributes, and object-level authorities involves great effort, increasing the likelihood of human error and resulting in the unfortunate reality that reviews will be performed neither consistently nor in a timely fashion. Security settings are less likely to become non-compliant when checks are conducted more frequently and with a consistent process.
Introducing Policy Minder! You can define rules indicating how the server's security should be configured, or simply take a snapshot of the current configuration to establish the desired baseline, and Policy Minder will quickly and accurately compare it to the server's current state and report on inconsistencies. Available for IBM i, AIX, and Linux, Policy Minder also provides the option to automatically correct many of those inconsistencies as shown in Figure 1.
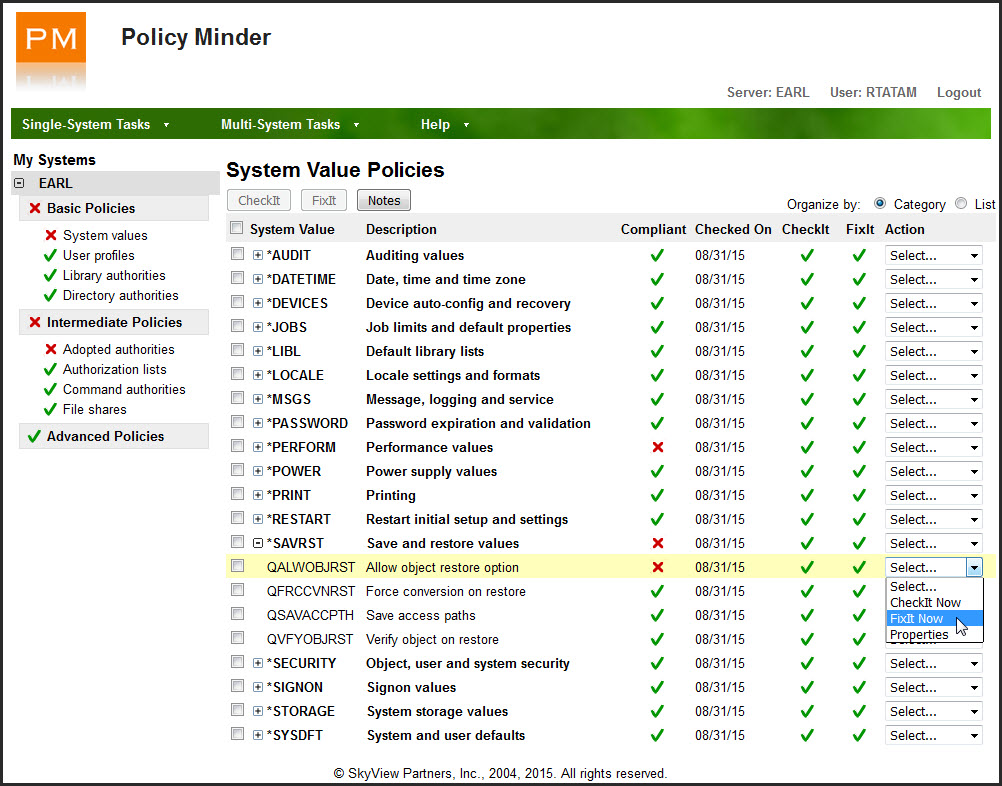
Figure 1: Policy Minder reports and fixes non-compliant items.
You get relief from verifying that critical network exit programs are still registered and knowing when new libraries or user profiles are created. Policy Minder eliminates the burden of determining if *PUBLIC and private authority is correctly set on thousands of database objects. You can breathe easier knowing special authorities are granted only to system administrators and that no unnecessary—and perhaps unauthorized—file shares have been created to the Integrated File System (IFS). All of this is possible without a programmer writing a single line of code.
Here’s a partial list of the configuration attributes Policy Minder can manage:







LATEST COMMENTS
MC Press Online